Dude, Where’s My Computer?
Headline: Cryptojacking
Date: 3/2/2022
Body:
What is Cryptojacking?
Cryptojacking is a new word that refers to a new kind of crime. Technically, it is the unauthorized use of other Peoples’ devices. These hackers take over the computers and cell phones and use them to create a network to more effectively mine cryptocurrency. This is kind of like the “zombie computer” spread of a virus, but in this case, the computers being co-opted are being tasked to mine cryptocurrency instead of spreading a virus. It is important to note that the aim is to keep this co-opting hidden from the local users so that the hijacker can use the increased computing power without additional expenses for electrical power.
Is this really a big deal?
Yes, there are 2 potentially significant effects:
- A decrease in speed and performance of your computer or network.
- A significant increase in electricity usage. Before you shrug this off, consider that the Bitcoin network currently uses more than 73TWh of energy each year. In addition to increasing energy bills, this could potentially add a significant amount of heat that will damage your computer or network.
Is this problem getting larger or smaller?
This is one way to start a fight at a cybersecurity conference. Some say that due to the efforts of police agencies and the shutdown of Coinhive, the problem is being mitigated. But the severity of the problem can quickly ramp back up when the value of cryptocurrency begins to climb. According to one security expert, “When we did our midyear threat report for 2018 we found that Cryptojacking had a 35 percent share of all web threats and that is honestly absolutely insane,” says Tyler Moffitt, senior threat researcher at the security firm Webroot. “This is a new threat that just came out in late September 2017. Even if it drops down to 25 percent by the end of the year, it’s still clearly a force to be reckoned with.”
How does this malicious code make its way onto a network or computer?
There are 2 main techniques that hackers use:
- People who are not very careful, click on a link and cryptomining code is installed.
- If a website is infected with JavaScript coding, it can be co-opted. When you visit the site, the malicious code is installed on your machine.
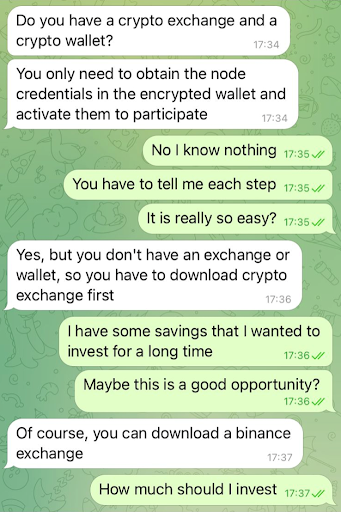
- Please note that sometimes, we say “yes” to limited Cryptojacking. For instance, assume that there was this site where you do gaming. Before you log on, the site may ask for your permission to use your computer for mining, while you are on the site. If they stop using your machine when you leave, this is permissible. But, to be honest, it’s difficult to know for sure whether they use our machines when we are logged off, so, be aware of the risk/reward tradeoff.
Have there been well known examples of Cryptojacking?
Yes. 2018 appears to have been the high-water mark, but in 2019, eight different apps were kicked out of the Microsoft Store site because Cryptojacking software was suspected to be active. In 2018, there was an intrusion into the LA Times Homicide Report page, one attack on a European Water utility control system, and there were multiple issues regarding Coinhive.
How can I tell if there is Cryptojacking going on?
| Symptom | Comment |
| Decreased Performance | If the computing cycles are being used to solve these math problems, there will be many less to run your software, and you will be likely to detect a lag. |
| Overheating | Cryptomining is a resource-intensive process. You will likely notice that your device is running hotter than usual. Much electrical power is used in cryptomining, so, if Cryptojacking is an issue, your processer will run hot and you might notice that your energy bill is a little higher than you would expect. |
| CPU Usage is not in proportion to the immersive nature of the site. | If you are visiting a site that is very basic and has a few small pictures and no video, your CPU usage should stay minimal. If it is working hard for no apparent reason, there could be Cryptojacking afoot. |
So, how can I prevent Cryptojacking on my machine?
There are a few preventative measures. Many of these might seem pedantic, but the are all important, just like eating your vegetables.
- Get a good security program to protect your machine from viruses and malware, and keep it up to date with patches and updates.
- Be aware of the newest Cryptojacking techniques: Most cryptojackers are not too creative. They will often hop on to a trend and use this one technique for as long as they can.
- Use browser extensions to control Cryptojacking attempts.
- Use AdBlocker software.
- Disable JavaScript. Websites that have Cryptojacking software will often code it in JavaScript, so if it doesn’t “work” on your machine, then, there is no chance for Cryptojacking.
- Block pages where Cryptojacking is very likely. Porn sites are very likely users of Cryptojacking software. But, there are others too. (Prepper websites are notorious for this activity too, so, be aware.)
- The biggest key here appears to be user training. Your end users have to be trained how to avoid phishing attacks and to detect other forms of social engineering. Often, cyberjacking software and other malware (e.g. ransomware) will ride in on the same permission given when they click an innocent looking link.
The Verdict
OK, I am not a cyber-security expert, and I don’t play one on my own video-blog either, but it seems that a few commonsense approaches can be of use here. Don’t click on any links for e-mails from unknown sources (e.g. don’t take candy from strangers either.) Since you are likely not a cyber-security professional either, be sure to get the benefits of having one on staff by signing up for a Web security program. (Kaspersky has been noted often in these readings, but WebRoot, Symantec and others are good too. Once again, Ben Franklin was right, an ounce of prevention is worth a pound of cure.
REFERENCES
https://www.kaspersky.com/resource-center/definitions/what-is-cryptojacking
https://www.crowdstrike.com/cybersecurity-101/cryptojacking/
https://www.wired.com/story/cryptojacking-took-over-internet/
Editor’s Note: Please note that the information contained herein is meant only for general education: This should not be construed as Tax Advice. Personal attributes could make a material difference in the advice given, so, before taking action, please consult your tax advisor or CPA.